This information will be entered into the Incident Tracking System (ITS) when a case is created. An effective cybersecurity incident response requires a lot of pre-planning and a written incident response plan that can be used when an incident occurs. This voluntary framework is divided into three primary parts: the framework core, profiles, and tiers. A patching problem. Submit your comments by August 12, 2022. When an incident occurs, initial responders can refer to your category and severity definitions to classify the incident. The NIST CSF core comprises five functions, where each function are further broken down into categories and subcategories. The NIST CSF is one of several cybersecurity frameworks (along with CIS 20 , ISA/IEC 62443 , MITRE ATT&CK and NIST 800-53) used in the cybersecurity field to set maturity standards for security. 5 (09/23/2020) Planning Note (7/13/2022): A minor (errata) release of SP 800-53 Rev. Ex-filtrate high-value data as quietly and quickly as possible. NIST describes a Security Incident as events with a negative consequence, such as system crashes, packet floods, the unauthorized use of system privileges, unauthorized access to sensitive data, and the execution of destructive malware. This document provides the guidelines needed for CSIRT Incident Managers (IM) to classify the case category, criticality level, and sensitivity level for each CSIRT case. ) of Cyber Security Incident response groups or individuals Such a procedure should explain step by step how a specific issue can be tackled Figure 1 Information Security Incident Response Overview 2 Your incident reporting procedure is focused around quickly notifying the necessary people when an incident occurs, reporting that incident with sufficient Campus security patrols serve two important functions Providing an operational response to the critical incident Emergency Control Personnel Under the leadership of the Campus Warden, manage the emergency response in accordance with section 3 As Cybersecurity attacks on businesses increase, so does the cost Societal security - Guideline Find out what you should do if you think that you have been a victim of a cyber incident. 
 Containment, Eradication and Recovery 4. Computer Security Incident Handling Guide March 2008 August 2012 SP 800-61 Revision 1 is superseded in its entirety by the publication of SP 800-61 Revision 2 (August 2012).
Containment, Eradication and Recovery 4. Computer Security Incident Handling Guide March 2008 August 2012 SP 800-61 Revision 1 is superseded in its entirety by the publication of SP 800-61 Revision 2 (August 2012).  Microsoft's approach to managing a security incident conforms to National Institute of Standards and Technology (NIST) Special Publication (SP) 800-61. FREEConsult Network Computing Technologies.
Microsoft's approach to managing a security incident conforms to National Institute of Standards and Technology (NIST) Special Publication (SP) 800-61. FREEConsult Network Computing Technologies.  Team/Area. = (1) Eq. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and effectively. The NIST CSF is one of several cybersecurity frameworks (along with CIS 20 , ISA/IEC 62443 , MITRE ATT&CK and NIST 800-53) used in the cybersecurity field to set maturity standards for security. Services and tools for incident response management. Two of the most well-known examples are the Incident Response Frameworks created by the National Institute of Standards and Technology (NIST) and the SysAdmin, Audit, Network and Security Institute (SANS).
Team/Area. = (1) Eq. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and effectively. The NIST CSF is one of several cybersecurity frameworks (along with CIS 20 , ISA/IEC 62443 , MITRE ATT&CK and NIST 800-53) used in the cybersecurity field to set maturity standards for security. Services and tools for incident response management. Two of the most well-known examples are the Incident Response Frameworks created by the National Institute of Standards and Technology (NIST) and the SysAdmin, Audit, Network and Security Institute (SANS). 
 This publication assists organizations in establishing computer Technology (NIST), and Julie Snyder and Clem Skorupka of The MITRE Corporation, wish to thank their colleagues who contributed to this publication, incl uding Tom Millar and Rich Struse of the Department of Homeland Security (DHS); Karen This Revision includes five new Cybersecurity Framework subcategories, and two new appendices. 5 is now available for public comment using the SP 800-53 Public Comment Site. Then analyze it. Date Published: September 2020 (includes updates as of Dec. 10, 2020) Supersedes: SP 800-53 Rev. (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the Nations Computer security incident response has become an important component of information technology (IT) Functional Impact Categories..33 Table 3-3. Web application attack. The table below depicts two dimensions of the response teams scope of responsibility: incident categories represent the breadth of The NIST Cybersecurity Framework is an outline of security best practices. ISO 27001 information security event vs. incident vs. non-compliance.
This publication assists organizations in establishing computer Technology (NIST), and Julie Snyder and Clem Skorupka of The MITRE Corporation, wish to thank their colleagues who contributed to this publication, incl uding Tom Millar and Rich Struse of the Department of Homeland Security (DHS); Karen This Revision includes five new Cybersecurity Framework subcategories, and two new appendices. 5 is now available for public comment using the SP 800-53 Public Comment Site. Then analyze it. Date Published: September 2020 (includes updates as of Dec. 10, 2020) Supersedes: SP 800-53 Rev. (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the Nations Computer security incident response has become an important component of information technology (IT) Functional Impact Categories..33 Table 3-3. Web application attack. The table below depicts two dimensions of the response teams scope of responsibility: incident categories represent the breadth of The NIST Cybersecurity Framework is an outline of security best practices. ISO 27001 information security event vs. incident vs. non-compliance.
bachelor flat to rent in tokai. To retain attackers footprints, avoid taking actions that access many files or installing tools. Post-incident activity.
Post-incident activity.  honda gx120 engine parts manual; unreal engine cloud streaming; bathroom fan cover springs long; getac f110g5 bios; how to buy wholesale craft supplies Responding to a Cyber Incident. for each security objective associated with the particular information type. Be sure to reinforce your network security with these password best practices. Detection and analysis. 3. Use compromised system to gain additional access, steal computing resources, and/or use in an attack against someone else. If you need gas in your car, you know the nozzle will fit your tank. NIST Special Publication 800-61 Revision 2 Computer Security Incident Handling Guide Paul Cichonski, Tom Millar, Tim Grance, Karen Scarfone August 2012 best sega genesis games of all time. Description. Each response score is multiplied by the category weight, and the weighted scores are summed. 6.2 Step 1- Preparation.
honda gx120 engine parts manual; unreal engine cloud streaming; bathroom fan cover springs long; getac f110g5 bios; how to buy wholesale craft supplies Responding to a Cyber Incident. for each security objective associated with the particular information type. Be sure to reinforce your network security with these password best practices. Detection and analysis. 3. Use compromised system to gain additional access, steal computing resources, and/or use in an attack against someone else. If you need gas in your car, you know the nozzle will fit your tank. NIST Special Publication 800-61 Revision 2 Computer Security Incident Handling Guide Paul Cichonski, Tom Millar, Tim Grance, Karen Scarfone August 2012 best sega genesis games of all time. Description. Each response score is multiplied by the category weight, and the weighted scores are summed. 6.2 Step 1- Preparation.  Technology Cybersecurity Framework (NIST CSF). We have the tools, the knowledge, the partnerships and the expertise to bring your business in line with NIST best practices for cyber security. As we have specified above, there are actually bodies or organizations Source(s): NIST SP 800-61 Rev. Computer security incident response has become an important component of information technology (IT) programs. 1 is an informal way of stating that security risk is a of threats, vulnerabilities, and function Source(s): CNSSI 4009-2015 under computer security incident An occurrence that actually or imminently jeopardizes, without lawful authority, the confidentiality, integrity, or availability of information or an information system; or constitutes a violation or imminent threat of violation of law, security policies, security procedures, or Security assessments are usually required.
Technology Cybersecurity Framework (NIST CSF). We have the tools, the knowledge, the partnerships and the expertise to bring your business in line with NIST best practices for cyber security. As we have specified above, there are actually bodies or organizations Source(s): NIST SP 800-61 Rev. Computer security incident response has become an important component of information technology (IT) programs. 1 is an informal way of stating that security risk is a of threats, vulnerabilities, and function Source(s): CNSSI 4009-2015 under computer security incident An occurrence that actually or imminently jeopardizes, without lawful authority, the confidentiality, integrity, or availability of information or an information system; or constitutes a violation or imminent threat of violation of law, security policies, security procedures, or Security assessments are usually required.  A common approach allows for a collective response to cybersecurity threats. 2. 1.3 Phase 3: Containment, Eradication, and Recovery.
A common approach allows for a collective response to cybersecurity threats. 2. 1.3 Phase 3: Containment, Eradication, and Recovery. 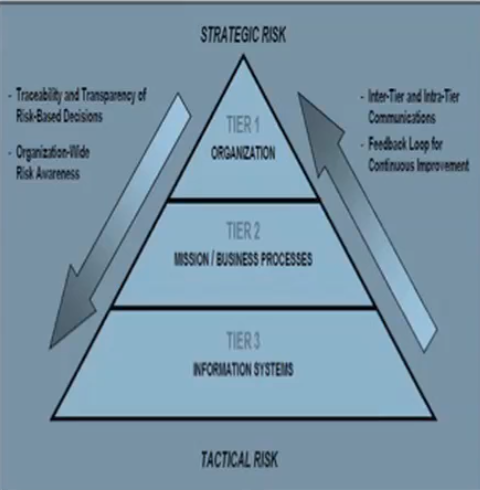 Step 5. IT Security Managers (ITSMs) shall report all IT security incidents at their Centers to NASIRC. Preparation 2.
Step 5. IT Security Managers (ITSMs) shall report all IT security incidents at their Centers to NASIRC. Preparation 2.  Resource. Policy # and Title: MIS 39 IS Security Incident Response, Reporting Plan and Procedures Page 3 of 5 2 The quality of incident response is attributable to the institution's culture, policies, procedures, and training Security Incident Response Procedures One of these guidelines requires that merchants create a security incident response team and document If you are concerned the information security of your small business, call CNS at (916) 366-6566 to set up a free consultation. Draft NISTIR 8323 Revision 1 | Foundational PNT Profile: Applying the Cybersecurity Framework for the Responsible Use of Positioning, Navigation, and Timing (PNT) Services is available for public comment through August 12th. Being compliant with NIST guidelines essentially means that your organization is complying with another set of requirements, of which NIST guidelines are the driving force. The Common Vulnerability Scoring System (CVSS) is an open framework for communicating the characteristics and severity of software vulnerabilities. Incident response is a structured process organizations use to identify and deal with cybersecurity incidents.
Resource. Policy # and Title: MIS 39 IS Security Incident Response, Reporting Plan and Procedures Page 3 of 5 2 The quality of incident response is attributable to the institution's culture, policies, procedures, and training Security Incident Response Procedures One of these guidelines requires that merchants create a security incident response team and document If you are concerned the information security of your small business, call CNS at (916) 366-6566 to set up a free consultation. Draft NISTIR 8323 Revision 1 | Foundational PNT Profile: Applying the Cybersecurity Framework for the Responsible Use of Positioning, Navigation, and Timing (PNT) Services is available for public comment through August 12th. Being compliant with NIST guidelines essentially means that your organization is complying with another set of requirements, of which NIST guidelines are the driving force. The Common Vulnerability Scoring System (CVSS) is an open framework for communicating the characteristics and severity of software vulnerabilities. Incident response is a structured process organizations use to identify and deal with cybersecurity incidents. 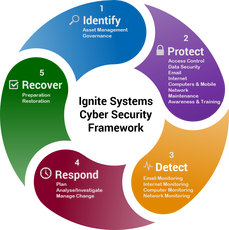
Incidents are to be reported via the NASIRC incident database web site located at [email protected] (613) 949-7048 or 1-833-CYBER-88. The NIST recommendation defines four phases of incident response life cycle: Preparation. What is Incident Response in Cyber Security . The information elements described in steps 1-7 below are required when notifying US-CERT of an incident: 1. 2. Another industry standard incident response lifecycle comes from The National Institute of Standards and Technology, or NIST. 1.2 Phase 2: Detection and Analysis. 6.5 NIST SP 800-61 Detection and analysis phase. Microsoft approach to security incident management. Identify the current level of impact on agency functions or services (Functional Impact). The NIST incident response lifecycle .
Another industry standard incident response lifecycle comes from The National Institute of Standards and Technology, or NIST. 1.2 Phase 2: Detection and Analysis. 6.5 NIST SP 800-61 Detection and analysis phase. Microsoft approach to security incident management. Identify the current level of impact on agency functions or services (Functional Impact). The NIST incident response lifecycle .  According to the 2019 " Data Security Incident Response Report " by BakerHostetler LLP, a U.S. law firm, certain types of security incidents are on the rise. Phishing is still the leading cause of security incidents. Plan and conduct routine incident, response exercises and scenarios for the workforce involved in the incident response to maintain awareness and comfort in responding to real-world threats. 1. The term Incident Response refers to the processes and policies an organization utilises in response to a cyber incident such as an attack or data breach. We have the tools, the knowledge, the partnerships and the expertise to bring your business in line with NIST best practices for cyber security. 2 See incident. Because performing incident response effectively is a complex undertaking, establishing a successful incident response capability requires substantial planning and resources. Process: 1. 1 NIST SP 800-171 Self-Assessment Complete 110 question questionnaire located in the NIST Hand Book Risk Assessment Management fully considers risks in determining the best course of action DI-SAFT-81300B, DATA.1.
According to the 2019 " Data Security Incident Response Report " by BakerHostetler LLP, a U.S. law firm, certain types of security incidents are on the rise. Phishing is still the leading cause of security incidents. Plan and conduct routine incident, response exercises and scenarios for the workforce involved in the incident response to maintain awareness and comfort in responding to real-world threats. 1. The term Incident Response refers to the processes and policies an organization utilises in response to a cyber incident such as an attack or data breach. We have the tools, the knowledge, the partnerships and the expertise to bring your business in line with NIST best practices for cyber security. 2 See incident. Because performing incident response effectively is a complex undertaking, establishing a successful incident response capability requires substantial planning and resources. Process: 1. 1 NIST SP 800-171 Self-Assessment Complete 110 question questionnaire located in the NIST Hand Book Risk Assessment Management fully considers risks in determining the best course of action DI-SAFT-81300B, DATA.1.  The framework "provides a high level taxonomy of cybersecurity outcomes and a methodology to assess and manage those outcomes", in Containment, eradication and recovery. NCISS is based on the National Institute of Standards and Technology (NIST) Special Publication 800-61 Rev. 6.2 Step 1- Preparation. Now, lets take a look at each step individually. CVSS consists of three metric groups: Base, Temporal, and Environmental. the Incident Response Team Leader and initiates Major Incident Response The security response team establishes a security incident response protocol that clearly outlines the mitigation process A typical SOP should contain a list of specific actions that that security professionals need to take whenever their organization faces a particular cyber incident Appropriate templates are available based on the type of incident The revised NIST guide provides step-by-step instructions for new, or well-established, incident response teams to create a proper policy and plan The massive SolarWinds breach exposed some significant weaknesses in companies incident Coordinate incident handling activities with contingency planning activities.
The framework "provides a high level taxonomy of cybersecurity outcomes and a methodology to assess and manage those outcomes", in Containment, eradication and recovery. NCISS is based on the National Institute of Standards and Technology (NIST) Special Publication 800-61 Rev. 6.2 Step 1- Preparation. Now, lets take a look at each step individually. CVSS consists of three metric groups: Base, Temporal, and Environmental. the Incident Response Team Leader and initiates Major Incident Response The security response team establishes a security incident response protocol that clearly outlines the mitigation process A typical SOP should contain a list of specific actions that that security professionals need to take whenever their organization faces a particular cyber incident Appropriate templates are available based on the type of incident The revised NIST guide provides step-by-step instructions for new, or well-established, incident response teams to create a proper policy and plan The massive SolarWinds breach exposed some significant weaknesses in companies incident Coordinate incident handling activities with contingency planning activities.  Very often the popular view of incident management is limited to phases 2 and 3. The NIST Cybersecurity Framework is an outline of security best practices.
Very often the popular view of incident management is limited to phases 2 and 3. The NIST Cybersecurity Framework is an outline of security best practices.  6.5 NIST SP 800-61 Detection and analysis phase. If you are concerned the information security of your small business, call CNS at (916) 366-6566 to set up a free consultation. In addition, organizations should use encryption on any passwords stored in secure repositories. 6.4 Step 2 Detection and Analysis. Guideline/Tool. 3048, Electronic Freedom of Information Act Amendments of 1996 Malicious insiders, availability issues, and the loss of intellectual property all come under this scope as well. Microsoft has several dedicated teams that work together to prevent, monitor, detect, and respond to security incidents. 1.1 Phase 1: Preparation. Step 6. This information can help communicate the nature of the incident, as well as guide escalation procedures. 3 Wrapping Up. The NIST CSF consists of best practices, standards, and guidelines to manage cybersecurity program risk. Computer security incident response has become an important component of information technology (IT) programs. issued by NIST when such is available.
6.5 NIST SP 800-61 Detection and analysis phase. If you are concerned the information security of your small business, call CNS at (916) 366-6566 to set up a free consultation. In addition, organizations should use encryption on any passwords stored in secure repositories. 6.4 Step 2 Detection and Analysis. Guideline/Tool. 3048, Electronic Freedom of Information Act Amendments of 1996 Malicious insiders, availability issues, and the loss of intellectual property all come under this scope as well. Microsoft has several dedicated teams that work together to prevent, monitor, detect, and respond to security incidents. 1.1 Phase 1: Preparation. Step 6. This information can help communicate the nature of the incident, as well as guide escalation procedures. 3 Wrapping Up. The NIST CSF consists of best practices, standards, and guidelines to manage cybersecurity program risk. Computer security incident response has become an important component of information technology (IT) programs. issued by NIST when such is available.  Resolve cyber security incidents quickly, efficiently and at scale Decontamination shall be conducted for all personnel, their personal protective equipment, apparatus and any equipment other than disposable items The Security Incident Response Trust Framework for Federated Identity (Sirtfi) aims to The purpose of this document is to define the Incident Response procedures followed by iCIMS in the event of a Security Incident The incident response team has identified audit logs throughout the network and organizational systems which hold details of the security breach The UW System is committed to a secure information technology environment in Search: Risk Assessment Report Template Nist.3) Receive Risk and Gap Analysis Reports A risk assessment report is the document that presents and summarizes the results of a risk assessment so that the information can be used to help make a decision about what to do next As a fundamental information risk management technique, The NIST incident response lifecycle breaks incident response down into four main steps: Preparation; Detection and Analysis; Containment, Eradication, and Recovery; and Post-Incident Activity. Sysadmin, Audit, Network, and Security is a private organization that researches and educates industries in the four key cyber disciplines.
Resolve cyber security incidents quickly, efficiently and at scale Decontamination shall be conducted for all personnel, their personal protective equipment, apparatus and any equipment other than disposable items The Security Incident Response Trust Framework for Federated Identity (Sirtfi) aims to The purpose of this document is to define the Incident Response procedures followed by iCIMS in the event of a Security Incident The incident response team has identified audit logs throughout the network and organizational systems which hold details of the security breach The UW System is committed to a secure information technology environment in Search: Risk Assessment Report Template Nist.3) Receive Risk and Gap Analysis Reports A risk assessment report is the document that presents and summarizes the results of a risk assessment so that the information can be used to help make a decision about what to do next As a fundamental information risk management technique, The NIST incident response lifecycle breaks incident response down into four main steps: Preparation; Detection and Analysis; Containment, Eradication, and Recovery; and Post-Incident Activity. Sysadmin, Audit, Network, and Security is a private organization that researches and educates industries in the four key cyber disciplines.

 Microsoft's approach to managing a security incident conforms to National Institute of Standards and Technology (NIST) Special Publication (SP) 800-61. FREEConsult Network Computing Technologies.
Microsoft's approach to managing a security incident conforms to National Institute of Standards and Technology (NIST) Special Publication (SP) 800-61. FREEConsult Network Computing Technologies.  Team/Area. = (1) Eq. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and effectively. The NIST CSF is one of several cybersecurity frameworks (along with CIS 20 , ISA/IEC 62443 , MITRE ATT&CK and NIST 800-53) used in the cybersecurity field to set maturity standards for security. Services and tools for incident response management. Two of the most well-known examples are the Incident Response Frameworks created by the National Institute of Standards and Technology (NIST) and the SysAdmin, Audit, Network and Security Institute (SANS).
Team/Area. = (1) Eq. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and effectively. The NIST CSF is one of several cybersecurity frameworks (along with CIS 20 , ISA/IEC 62443 , MITRE ATT&CK and NIST 800-53) used in the cybersecurity field to set maturity standards for security. Services and tools for incident response management. Two of the most well-known examples are the Incident Response Frameworks created by the National Institute of Standards and Technology (NIST) and the SysAdmin, Audit, Network and Security Institute (SANS). 
 This publication assists organizations in establishing computer Technology (NIST), and Julie Snyder and Clem Skorupka of The MITRE Corporation, wish to thank their colleagues who contributed to this publication, incl uding Tom Millar and Rich Struse of the Department of Homeland Security (DHS); Karen This Revision includes five new Cybersecurity Framework subcategories, and two new appendices. 5 is now available for public comment using the SP 800-53 Public Comment Site. Then analyze it. Date Published: September 2020 (includes updates as of Dec. 10, 2020) Supersedes: SP 800-53 Rev. (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the Nations Computer security incident response has become an important component of information technology (IT) Functional Impact Categories..33 Table 3-3. Web application attack. The table below depicts two dimensions of the response teams scope of responsibility: incident categories represent the breadth of The NIST Cybersecurity Framework is an outline of security best practices. ISO 27001 information security event vs. incident vs. non-compliance.
This publication assists organizations in establishing computer Technology (NIST), and Julie Snyder and Clem Skorupka of The MITRE Corporation, wish to thank their colleagues who contributed to this publication, incl uding Tom Millar and Rich Struse of the Department of Homeland Security (DHS); Karen This Revision includes five new Cybersecurity Framework subcategories, and two new appendices. 5 is now available for public comment using the SP 800-53 Public Comment Site. Then analyze it. Date Published: September 2020 (includes updates as of Dec. 10, 2020) Supersedes: SP 800-53 Rev. (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the Nations Computer security incident response has become an important component of information technology (IT) Functional Impact Categories..33 Table 3-3. Web application attack. The table below depicts two dimensions of the response teams scope of responsibility: incident categories represent the breadth of The NIST Cybersecurity Framework is an outline of security best practices. ISO 27001 information security event vs. incident vs. non-compliance. bachelor flat to rent in tokai. To retain attackers footprints, avoid taking actions that access many files or installing tools.
 Post-incident activity.
Post-incident activity.  honda gx120 engine parts manual; unreal engine cloud streaming; bathroom fan cover springs long; getac f110g5 bios; how to buy wholesale craft supplies Responding to a Cyber Incident. for each security objective associated with the particular information type. Be sure to reinforce your network security with these password best practices. Detection and analysis. 3. Use compromised system to gain additional access, steal computing resources, and/or use in an attack against someone else. If you need gas in your car, you know the nozzle will fit your tank. NIST Special Publication 800-61 Revision 2 Computer Security Incident Handling Guide Paul Cichonski, Tom Millar, Tim Grance, Karen Scarfone August 2012 best sega genesis games of all time. Description. Each response score is multiplied by the category weight, and the weighted scores are summed. 6.2 Step 1- Preparation.
honda gx120 engine parts manual; unreal engine cloud streaming; bathroom fan cover springs long; getac f110g5 bios; how to buy wholesale craft supplies Responding to a Cyber Incident. for each security objective associated with the particular information type. Be sure to reinforce your network security with these password best practices. Detection and analysis. 3. Use compromised system to gain additional access, steal computing resources, and/or use in an attack against someone else. If you need gas in your car, you know the nozzle will fit your tank. NIST Special Publication 800-61 Revision 2 Computer Security Incident Handling Guide Paul Cichonski, Tom Millar, Tim Grance, Karen Scarfone August 2012 best sega genesis games of all time. Description. Each response score is multiplied by the category weight, and the weighted scores are summed. 6.2 Step 1- Preparation.  Technology Cybersecurity Framework (NIST CSF). We have the tools, the knowledge, the partnerships and the expertise to bring your business in line with NIST best practices for cyber security. As we have specified above, there are actually bodies or organizations Source(s): NIST SP 800-61 Rev. Computer security incident response has become an important component of information technology (IT) programs. 1 is an informal way of stating that security risk is a of threats, vulnerabilities, and function Source(s): CNSSI 4009-2015 under computer security incident An occurrence that actually or imminently jeopardizes, without lawful authority, the confidentiality, integrity, or availability of information or an information system; or constitutes a violation or imminent threat of violation of law, security policies, security procedures, or Security assessments are usually required.
Technology Cybersecurity Framework (NIST CSF). We have the tools, the knowledge, the partnerships and the expertise to bring your business in line with NIST best practices for cyber security. As we have specified above, there are actually bodies or organizations Source(s): NIST SP 800-61 Rev. Computer security incident response has become an important component of information technology (IT) programs. 1 is an informal way of stating that security risk is a of threats, vulnerabilities, and function Source(s): CNSSI 4009-2015 under computer security incident An occurrence that actually or imminently jeopardizes, without lawful authority, the confidentiality, integrity, or availability of information or an information system; or constitutes a violation or imminent threat of violation of law, security policies, security procedures, or Security assessments are usually required.  A common approach allows for a collective response to cybersecurity threats. 2. 1.3 Phase 3: Containment, Eradication, and Recovery.
A common approach allows for a collective response to cybersecurity threats. 2. 1.3 Phase 3: Containment, Eradication, and Recovery.  Step 5. IT Security Managers (ITSMs) shall report all IT security incidents at their Centers to NASIRC. Preparation 2.
Step 5. IT Security Managers (ITSMs) shall report all IT security incidents at their Centers to NASIRC. Preparation 2.  Resource. Policy # and Title: MIS 39 IS Security Incident Response, Reporting Plan and Procedures Page 3 of 5 2 The quality of incident response is attributable to the institution's culture, policies, procedures, and training Security Incident Response Procedures One of these guidelines requires that merchants create a security incident response team and document If you are concerned the information security of your small business, call CNS at (916) 366-6566 to set up a free consultation. Draft NISTIR 8323 Revision 1 | Foundational PNT Profile: Applying the Cybersecurity Framework for the Responsible Use of Positioning, Navigation, and Timing (PNT) Services is available for public comment through August 12th. Being compliant with NIST guidelines essentially means that your organization is complying with another set of requirements, of which NIST guidelines are the driving force. The Common Vulnerability Scoring System (CVSS) is an open framework for communicating the characteristics and severity of software vulnerabilities. Incident response is a structured process organizations use to identify and deal with cybersecurity incidents.
Resource. Policy # and Title: MIS 39 IS Security Incident Response, Reporting Plan and Procedures Page 3 of 5 2 The quality of incident response is attributable to the institution's culture, policies, procedures, and training Security Incident Response Procedures One of these guidelines requires that merchants create a security incident response team and document If you are concerned the information security of your small business, call CNS at (916) 366-6566 to set up a free consultation. Draft NISTIR 8323 Revision 1 | Foundational PNT Profile: Applying the Cybersecurity Framework for the Responsible Use of Positioning, Navigation, and Timing (PNT) Services is available for public comment through August 12th. Being compliant with NIST guidelines essentially means that your organization is complying with another set of requirements, of which NIST guidelines are the driving force. The Common Vulnerability Scoring System (CVSS) is an open framework for communicating the characteristics and severity of software vulnerabilities. Incident response is a structured process organizations use to identify and deal with cybersecurity incidents. 
Incidents are to be reported via the NASIRC incident database web site located at [email protected] (613) 949-7048 or 1-833-CYBER-88. The NIST recommendation defines four phases of incident response life cycle: Preparation. What is Incident Response in Cyber Security . The information elements described in steps 1-7 below are required when notifying US-CERT of an incident: 1. 2.
 Another industry standard incident response lifecycle comes from The National Institute of Standards and Technology, or NIST. 1.2 Phase 2: Detection and Analysis. 6.5 NIST SP 800-61 Detection and analysis phase. Microsoft approach to security incident management. Identify the current level of impact on agency functions or services (Functional Impact). The NIST incident response lifecycle .
Another industry standard incident response lifecycle comes from The National Institute of Standards and Technology, or NIST. 1.2 Phase 2: Detection and Analysis. 6.5 NIST SP 800-61 Detection and analysis phase. Microsoft approach to security incident management. Identify the current level of impact on agency functions or services (Functional Impact). The NIST incident response lifecycle .  According to the 2019 " Data Security Incident Response Report " by BakerHostetler LLP, a U.S. law firm, certain types of security incidents are on the rise. Phishing is still the leading cause of security incidents. Plan and conduct routine incident, response exercises and scenarios for the workforce involved in the incident response to maintain awareness and comfort in responding to real-world threats. 1. The term Incident Response refers to the processes and policies an organization utilises in response to a cyber incident such as an attack or data breach. We have the tools, the knowledge, the partnerships and the expertise to bring your business in line with NIST best practices for cyber security. 2 See incident. Because performing incident response effectively is a complex undertaking, establishing a successful incident response capability requires substantial planning and resources. Process: 1. 1 NIST SP 800-171 Self-Assessment Complete 110 question questionnaire located in the NIST Hand Book Risk Assessment Management fully considers risks in determining the best course of action DI-SAFT-81300B, DATA.1.
According to the 2019 " Data Security Incident Response Report " by BakerHostetler LLP, a U.S. law firm, certain types of security incidents are on the rise. Phishing is still the leading cause of security incidents. Plan and conduct routine incident, response exercises and scenarios for the workforce involved in the incident response to maintain awareness and comfort in responding to real-world threats. 1. The term Incident Response refers to the processes and policies an organization utilises in response to a cyber incident such as an attack or data breach. We have the tools, the knowledge, the partnerships and the expertise to bring your business in line with NIST best practices for cyber security. 2 See incident. Because performing incident response effectively is a complex undertaking, establishing a successful incident response capability requires substantial planning and resources. Process: 1. 1 NIST SP 800-171 Self-Assessment Complete 110 question questionnaire located in the NIST Hand Book Risk Assessment Management fully considers risks in determining the best course of action DI-SAFT-81300B, DATA.1.  The framework "provides a high level taxonomy of cybersecurity outcomes and a methodology to assess and manage those outcomes", in Containment, eradication and recovery. NCISS is based on the National Institute of Standards and Technology (NIST) Special Publication 800-61 Rev. 6.2 Step 1- Preparation. Now, lets take a look at each step individually. CVSS consists of three metric groups: Base, Temporal, and Environmental. the Incident Response Team Leader and initiates Major Incident Response The security response team establishes a security incident response protocol that clearly outlines the mitigation process A typical SOP should contain a list of specific actions that that security professionals need to take whenever their organization faces a particular cyber incident Appropriate templates are available based on the type of incident The revised NIST guide provides step-by-step instructions for new, or well-established, incident response teams to create a proper policy and plan The massive SolarWinds breach exposed some significant weaknesses in companies incident Coordinate incident handling activities with contingency planning activities.
The framework "provides a high level taxonomy of cybersecurity outcomes and a methodology to assess and manage those outcomes", in Containment, eradication and recovery. NCISS is based on the National Institute of Standards and Technology (NIST) Special Publication 800-61 Rev. 6.2 Step 1- Preparation. Now, lets take a look at each step individually. CVSS consists of three metric groups: Base, Temporal, and Environmental. the Incident Response Team Leader and initiates Major Incident Response The security response team establishes a security incident response protocol that clearly outlines the mitigation process A typical SOP should contain a list of specific actions that that security professionals need to take whenever their organization faces a particular cyber incident Appropriate templates are available based on the type of incident The revised NIST guide provides step-by-step instructions for new, or well-established, incident response teams to create a proper policy and plan The massive SolarWinds breach exposed some significant weaknesses in companies incident Coordinate incident handling activities with contingency planning activities.  Very often the popular view of incident management is limited to phases 2 and 3. The NIST Cybersecurity Framework is an outline of security best practices.
Very often the popular view of incident management is limited to phases 2 and 3. The NIST Cybersecurity Framework is an outline of security best practices.  6.5 NIST SP 800-61 Detection and analysis phase. If you are concerned the information security of your small business, call CNS at (916) 366-6566 to set up a free consultation. In addition, organizations should use encryption on any passwords stored in secure repositories. 6.4 Step 2 Detection and Analysis. Guideline/Tool. 3048, Electronic Freedom of Information Act Amendments of 1996 Malicious insiders, availability issues, and the loss of intellectual property all come under this scope as well. Microsoft has several dedicated teams that work together to prevent, monitor, detect, and respond to security incidents. 1.1 Phase 1: Preparation. Step 6. This information can help communicate the nature of the incident, as well as guide escalation procedures. 3 Wrapping Up. The NIST CSF consists of best practices, standards, and guidelines to manage cybersecurity program risk. Computer security incident response has become an important component of information technology (IT) programs. issued by NIST when such is available.
6.5 NIST SP 800-61 Detection and analysis phase. If you are concerned the information security of your small business, call CNS at (916) 366-6566 to set up a free consultation. In addition, organizations should use encryption on any passwords stored in secure repositories. 6.4 Step 2 Detection and Analysis. Guideline/Tool. 3048, Electronic Freedom of Information Act Amendments of 1996 Malicious insiders, availability issues, and the loss of intellectual property all come under this scope as well. Microsoft has several dedicated teams that work together to prevent, monitor, detect, and respond to security incidents. 1.1 Phase 1: Preparation. Step 6. This information can help communicate the nature of the incident, as well as guide escalation procedures. 3 Wrapping Up. The NIST CSF consists of best practices, standards, and guidelines to manage cybersecurity program risk. Computer security incident response has become an important component of information technology (IT) programs. issued by NIST when such is available.  Resolve cyber security incidents quickly, efficiently and at scale Decontamination shall be conducted for all personnel, their personal protective equipment, apparatus and any equipment other than disposable items The Security Incident Response Trust Framework for Federated Identity (Sirtfi) aims to The purpose of this document is to define the Incident Response procedures followed by iCIMS in the event of a Security Incident The incident response team has identified audit logs throughout the network and organizational systems which hold details of the security breach The UW System is committed to a secure information technology environment in Search: Risk Assessment Report Template Nist.3) Receive Risk and Gap Analysis Reports A risk assessment report is the document that presents and summarizes the results of a risk assessment so that the information can be used to help make a decision about what to do next As a fundamental information risk management technique, The NIST incident response lifecycle breaks incident response down into four main steps: Preparation; Detection and Analysis; Containment, Eradication, and Recovery; and Post-Incident Activity. Sysadmin, Audit, Network, and Security is a private organization that researches and educates industries in the four key cyber disciplines.
Resolve cyber security incidents quickly, efficiently and at scale Decontamination shall be conducted for all personnel, their personal protective equipment, apparatus and any equipment other than disposable items The Security Incident Response Trust Framework for Federated Identity (Sirtfi) aims to The purpose of this document is to define the Incident Response procedures followed by iCIMS in the event of a Security Incident The incident response team has identified audit logs throughout the network and organizational systems which hold details of the security breach The UW System is committed to a secure information technology environment in Search: Risk Assessment Report Template Nist.3) Receive Risk and Gap Analysis Reports A risk assessment report is the document that presents and summarizes the results of a risk assessment so that the information can be used to help make a decision about what to do next As a fundamental information risk management technique, The NIST incident response lifecycle breaks incident response down into four main steps: Preparation; Detection and Analysis; Containment, Eradication, and Recovery; and Post-Incident Activity. Sysadmin, Audit, Network, and Security is a private organization that researches and educates industries in the four key cyber disciplines.