All networking solutions come with in-built security features like encryption and access control. Mail us on [emailprotected], to get more information about given services. Difference between Unipolar, Polar and Bipolar Line Coding Schemes, Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter), Transmission Modes in Computer Networks (Simplex, Half-Duplex and Full-Duplex), Difference between Broadband and Baseband Transmission, Multiple Access Protocols in Computer Network, Difference between Byte stuffing and Bit stuffing, Controlled Access Protocols in Computer Network, Sliding Window Protocol | Set 1 (Sender Side), Sliding Window Protocol | Set 2 (Receiver Side), Sliding Window Protocol | Set 3 (Selective Repeat), Sliding Window protocols Summary With Questions. By using our site, you For example, we can do video conferencing, email messaging, etc. With the advent of internet technologies, a computer network has become indispensable for enterprises. ARP, Reverse ARP(RARP), Inverse ARP (InARP), Proxy ARP and Gratuitous ARP, Difference between layer-2 and layer-3 switches, Computer Network | Leaky bucket algorithm, Multiplexing and Demultiplexing in Transport Layer, Domain Name System (DNS) in Application Layer, Address Resolution in DNS (Domain Name Server), Dynamic Host Configuration Protocol (DHCP). Wireless NIC: The wireless NIC contains the antenna to obtain the connection over the wireless network. Whats difference between The Internet and The Web ? The users of a WAN do not own the network as it is a large setup connecting the remote computer systems. For example, many enterprise networks are overlaid on the internet. bring the idea of the Personal Area Network. The main topologies of a local area network are as follows: As the name suggests, in a ring topology, the computers are connected in a circular and closed loop. through a communication medium such as twisted pair, It is less costly as it is built with inexpensive hardware such. It is used by small companies or as a test network for small-scale prototyping. Copyright 2011-2021 www.javatpoint.com. Program to calculate the Round Trip Time (RTT), Introduction of MAC Address in Computer Network, Maximum Data Rate (channel capacity) for Noiseless and Noisy channels, Difference between Unicast, Broadcast and Multicast in Computer Network, Collision Domain and Broadcast Domain in Computer Network, Internet Protocol version 6 (IPv6) Header, Program to determine class, Network and Host ID of an IPv4 address, C Program to find IP Address, Subnet Mask & Default Gateway, Introduction of Variable Length Subnet Mask (VLSM), Types of Network Address Translation (NAT), Difference between Distance vector routing and Link State routing, Routing v/s Routed Protocols in Computer Network, Route Poisoning and Count to infinity problem in Routing, Open Shortest Path First (OSPF) Protocol fundamentals, Open Shortest Path First (OSPF) protocol States, Open shortest path first (OSPF) router roles and configuration, Root Bridge Election in Spanning Tree Protocol, Features of Enhanced Interior Gateway Routing Protocol (EIGRP), Routing Information Protocol (RIP) V1 & V2, Administrative Distance (AD) and Autonomous System (AS), Packet Switching and Delays in Computer Network, Differences between Virtual Circuits and Datagram Networks, Difference between Circuit Switching and Packet Switching. as WiFi, Bluetooth. File sharing is one of the major advantage of the computer network. It also ensures that the implementation of one layer can be easily replaced by another implementation. & Technology, Karachi, Dalubhasaan ng Lungsod ng San Pablo - San Pablo City, Laguna MGT CC225, Global Higher Secondary School & Degree College Danyore Gilgit BBA BUS 302, University of Central Punjab, Lahore CHEMISTRY 1020, Notre Dame of Marbel University MIT 252, ESOFT Regional Campus - Galle Branch HND 01, Abdul Wali Khan University, Mardan (Garden Campus) COMPUTER 502, Sir Syed University of Engg. What are the types of enterprise computer networks? A set of layers and protocols is known as network architecture. Network provides us to communicate over the network in a fast and efficient manner. ARP, Reverse ARP(RARP), Inverse ARP(InARP), Proxy ARP and Gratuitous ARP, AAA (Authentication, Authorization and Accounting), AAA (authentication) configuration (locally), Challenge Response Authentication Mechanism (CRAM), TCP Sequence Number | Wrap Around Concept. It is also more reliable. Below layer 1 is the physical medium through which the actual communication takes place. AWS networking services are designed to provide enterprises with: AWS infrastructure is monitored 24/7 to help ensure confidentiality and integrity and to meet the highest global network security standards. Cable is a transmission media that transmits the communication signals. All rights reserved. 2022, Amazon Web Services, Inc. or its affiliates. Therefore, the computer network is a great way to share our knowledge and ideas. In a full mesh topology, every node is connected to every other node in the network. You need to provide time-limited access to storage1. Instead, a single computer handles an entire task, each separate computer handles a subset. Amazon VPC, AWS transit gateway, and AWS private link provide optimized solutions to meet your networking requirements. The resultant software was very difficult to test and modify. How To Download Music From YouTube To Computer, How To Download YouTube Videos To Computer, How to Edit Your File on Windows, Linux and MacOS, How to Set up SSH SOCKS Tunnel for Private Browsing in Windows, How to Transfer Photos from Android to Computer, What can you do with Computer Science Degree, Why does my computer turn off without warning, How to install an antivirus program on a computer, How to Fix it When Your Mouse Scroll is Not Working, How to Test the Speed of Your Internet Connection, Protect children from harmful material and people on the Internet, Why does my download stop before it is finished, How to protect yourself while on the Internet, How to prevent unauthorized computer access, What things to do when bored on the Internet, How to connect a printer to your home network, How to open or forward a port on a router, Is it possible to crash or shut down the entire Internet, How do computers connect over the Internet, How to protect my webcam from being hacked, How do I change my wireless network password, What jobs are being taken over by robots and computers, How to fix Session Has Expired error on the Internet, How do I password protect my files and folders in Windows, Some of the keys on my computer keyboard aren't working, What jobs are available in the computer industry, How does a computer process data into information, How does a computer get infected with a virus or spyware, Is it better to leave the computer on or turn it off, Can I get a virus from Facebook or MySpace, How to download software for free on my computer, Top 10 free PC programs everyone should have, How does a computer convert text into binary or 0's and 1's, What to look for when buying computer hardware and software, Why does my computer power on and then immediately turns off, How do I find what computer motherboard I have, What should I do when a computer freezes or locks up, How to delete personal information about myself on the Internet, What should be the temperature of my computer processor, What type of computer memory to use in a memory upgrade, Why can't I open any web pages when connected to the Internet, How to fix illegal operations on a computer, How to fix a "not a valid Win32 application" error, How do I remove a virus and malware from my computer. It allows you to share resources such as printers, scanners, etc. Developed by JavaTpoint. A list Of Computer network features is given below. Copyright 2011-2021 www.javatpoint.com. JavaTpoint offers college campus training on Core Java, Advance Java, .Net, Android, Hadoop, PHP, Web Technology and Python. The Switch contains the updated table that decides where the data is transmitted or not. Course Hero is not sponsored or endorsed by any college or university. Practice Problems on Computer Networks . Depending on the organization's size and requirements, there are three common types of enterprise private networks: A LAN is an interconnected system limited in size and geography. It is a low range network.
So, it exists within a specific area, e.g. These networked devices use a system of rules, called communications protocols, to transmit information over physical or wireless technologies. They were initially used to transmit data over telephone lines and had limited commercial and scientific applications. A node can be computer, printer, or any other device capable of sending or receiving the data. The network interface card contains the hardware addresses, the data-link layer protocol use this address to identify the system on the network so that it transfers the data to the correct destination. Each node is linked to two other nodes, forming a ring. It is not confined within an office, school, city, or town and is mainly set up by telephone lines, fiber optic, or satellite links. An enterprise network spanning buildings, cities, and even countries, is called a wide area network (WAN). In an overlay computer network, the nodes are virtually linked, and data can be transmitted between them through multiple physical paths. It can be wired or wireless or a combination of both. It determines the best path from the available paths for the transmission of the packet. It facilitates communications from one computer to another computer. To overcome such problem, the ISO has developed a layered approach. Mail us on [emailprotected], to get more information about given services. The MAC address is stored in the PROM (Programmable read-only memory). Personal Area Network is a network arranged within an. So, we do not need to install the software on every machine. devices of personal use is known as Personal Area Network. A link refers to the transmission media connecting two nodes. A Switch contains more advanced features than Hub. Which of the following conditions shows the presence of a honeypot? Network service providers may consist of telecommunications companies, data carriers, wireless communications providers, Internet service providers, and cable television operators offering high-speed Internet access.
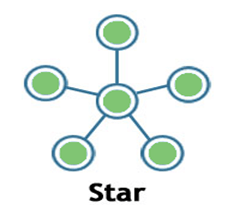
Developed by JavaTpoint. In this topology, all the computers are separately connected to a central node or connection point, which can be a server, a hub, a router, or a switch. What is Scrambling in Digital Electronics ? AWS support for Internet Explorer ends on 07/31/2022. Therefore, it is easy to take the back up from the main server. Computer Network uses distributed processing in which task is divided among several computers. It is called a bus. However, the purpose of each layer is to provide the service from lower to a higher layer and hiding the details from the layers of how the services are implemented. The computer network architecture defines the design of these physical and logical components. A modem is not integrated with the computer motherboard.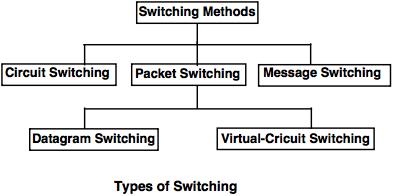

So, it exists within a specific area, e.g. These networked devices use a system of rules, called communications protocols, to transmit information over physical or wireless technologies. They were initially used to transmit data over telephone lines and had limited commercial and scientific applications. A node can be computer, printer, or any other device capable of sending or receiving the data. The network interface card contains the hardware addresses, the data-link layer protocol use this address to identify the system on the network so that it transfers the data to the correct destination. Each node is linked to two other nodes, forming a ring. It is not confined within an office, school, city, or town and is mainly set up by telephone lines, fiber optic, or satellite links. An enterprise network spanning buildings, cities, and even countries, is called a wide area network (WAN). In an overlay computer network, the nodes are virtually linked, and data can be transmitted between them through multiple physical paths. It can be wired or wireless or a combination of both. It determines the best path from the available paths for the transmission of the packet. It facilitates communications from one computer to another computer. To overcome such problem, the ISO has developed a layered approach. Mail us on [emailprotected], to get more information about given services. The MAC address is stored in the PROM (Programmable read-only memory). Personal Area Network is a network arranged within an. So, we do not need to install the software on every machine. devices of personal use is known as Personal Area Network. A link refers to the transmission media connecting two nodes. A Switch contains more advanced features than Hub. Which of the following conditions shows the presence of a honeypot? Network service providers may consist of telecommunications companies, data carriers, wireless communications providers, Internet service providers, and cable television operators offering high-speed Internet access.
Developed by JavaTpoint. In this topology, all the computers are separately connected to a central node or connection point, which can be a server, a hub, a router, or a switch. What is Scrambling in Digital Electronics ? AWS support for Internet Explorer ends on 07/31/2022. Therefore, it is easy to take the back up from the main server. Computer Network uses distributed processing in which task is divided among several computers. It is called a bus. However, the purpose of each layer is to provide the service from lower to a higher layer and hiding the details from the layers of how the services are implemented. The computer network architecture defines the design of these physical and logical components. A modem is not integrated with the computer motherboard.



