Eavesdropping can be passive or active: Detecting passive eavesdropping attacks is often more important than spotting active ones, since active attacks requires the attacker to gain knowledge of the friendly units by conducting passive eavesdropping before. threats cybersecurity cyber attacks cyberweapons malware It is also used directly by security teams when investigating incidents. In the United States alone, the attacks affected nine government agencies and more than 60,000 private businesses. Give users the option to disable client-side scripts. Get expert advice on enhancing security, data governance and IT operations. DDoS Protection Block attack traffic at the edge to ensure business continuity with guaranteed uptime and no performance impact.  Fileless malware resides in the devices RAM and typically access native operating system tools, like PowerShell and Windows Management Instrumentation (WMI) to inject malicious code.
Fileless malware resides in the devices RAM and typically access native operating system tools, like PowerShell and Windows Management Instrumentation (WMI) to inject malicious code.  The last method mentioned is executed in a systematic manner known as a brute-force attack. A brute-force attack employs a program to try all the possible variants and combinations of information to guess the password. security threats cyber examples transportation cybersecurity risks aviation industry chart systems airport attacks transport incidents radware terrorism rise many air This type of attack usually exploits security vulnerabilities in a network, such as an unsecured public WiFi, to insert themselves between a visitors device and the network. A message processed by a hash function produces a message digest (MD) of fixed length, independent of the length of the input message; this MD uniquely characterizes the message. The attacking computer substitutes its IP address for the trusted client while the server continues the session, believing it is communicating with the client. recovery cybersecurity disaster plan security template strategy
The last method mentioned is executed in a systematic manner known as a brute-force attack. A brute-force attack employs a program to try all the possible variants and combinations of information to guess the password. security threats cyber examples transportation cybersecurity risks aviation industry chart systems airport attacks transport incidents radware terrorism rise many air This type of attack usually exploits security vulnerabilities in a network, such as an unsecured public WiFi, to insert themselves between a visitors device and the network. A message processed by a hash function produces a message digest (MD) of fixed length, independent of the length of the input message; this MD uniquely characterizes the message. The attacking computer substitutes its IP address for the trusted client while the server continues the session, believing it is communicating with the client. recovery cybersecurity disaster plan security template strategy
Attackers take the time to conduct research into targets and create messages that are personal and relevant. To protect yourself from drive-by attacks, you need to keep your browsers and operating systems up to date and avoid websites that might contain malicious code. When the victim requests a page from the website, the website transmits the page, with the attackers payload as part of the HTML body, to the victims browser, which executes the malicious script. Convert special characters such as ?, &, /, <, > and spaces to their respective HTML or URL encoded equivalents. Data Risk Analysis Automate the detection of non-compliant, risky, or malicious data access behavior across all of your databases enterprise-wide to accelerate remediation. Another common method is the dictionary attack, when the attacker uses a list of common passwords to attempt to gain access to a users computer and network. The NotPetya attack hit targets around the world, with several waves continuing for more than a year, costing more than $10 billion in damage. Currently, there is no single technology or configuration to prevent all MitM attacks.
RFC3704 filtering, which will deny traffic from spoofed addresses and help ensure that traffic is traceable to its correct source network. Here are some of the most common types of malware: Ransomware Survivor: 6 Tips to Prevent Ransomware Attacks. Here are some common types of man-in-the-middle attacks: In this type of MitM attack, an attacker hijacks a session between a trusted client and network server. J2EE and ASP.NET applications are less likely to have easily exploited SQL injections because of the nature of the programmatic interfaces available. ![]() There are many types of malware, of which ransomware is just one variant. This causes the target system to time out while waiting for the response from the attackers device, which makes the system crash or become unusable when the connection queue fills up. infographic cyber attacks usa attack target governance facing startlingly developed comparitech levels according Therefore, SQL injections work mostly if a website uses dynamic SQL. Hackers look for insecure websites and plant a malicious script into HTTP or PHP code on one of the pages. In March 2021, a large-scale cyber attack was carried out against Microsoft Exchange, a popular enterprise email server. Because passwords are the most commonly used mechanism to authenticate users to an information system, obtaining passwords is a common and effective attack approach.
There are many types of malware, of which ransomware is just one variant. This causes the target system to time out while waiting for the response from the attackers device, which makes the system crash or become unusable when the connection queue fills up. infographic cyber attacks usa attack target governance facing startlingly developed comparitech levels according Therefore, SQL injections work mostly if a website uses dynamic SQL. Hackers look for insecure websites and plant a malicious script into HTTP or PHP code on one of the pages. In March 2021, a large-scale cyber attack was carried out against Microsoft Exchange, a popular enterprise email server. Because passwords are the most commonly used mechanism to authenticate users to an information system, obtaining passwords is a common and effective attack approach.
For example, RFC3704 filtering will drop packets from bogon list addresses. Imperva provides security solutions that protect organizations against all common cyber attacks. Mounting a good defense requires understanding the offense. 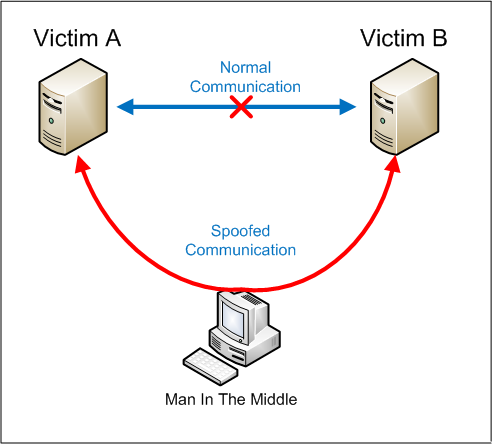 For example, it might send the victims cookie to the attackers server, and the attacker can extract it and use it for session hijacking. Man-in-the-Middle (MitM) attacks are breaches that allow attackers to intercept the data transmitted between networks, computers or users. Ping of death attacks can be blocked by using a firewall that will check fragmented IP packets for maximum size.
For example, it might send the victims cookie to the attackers server, and the attacker can extract it and use it for session hijacking. Man-in-the-Middle (MitM) attacks are breaches that allow attackers to intercept the data transmitted between networks, computers or users. Ping of death attacks can be blocked by using a firewall that will check fragmented IP packets for maximum size.
In July 2020, Twitter was breached by a group of three attackers, who took over popular Twitter accounts. The target site is flooded with illegitimate service requests and is forced to deny service to legitimate users. However, first-party cloud security tools are limited, and there is no guarantee that they are being used properly and all cloud resources are really secured. While cybersecurity prevention measures differ for each type of attack, good security practices and basic IT hygiene are generally good at mitigating these attacks. This was a massive, highly innovative supply chain attack detected in December 2020, and named after its victim, Austin-based IT management company SolarWinds. The target host might accept the packet and act upon it. cyber attacks Thus, preventing zero-day attacks requires constant monitoring, proactive detection, and agile threat management practices. To defend against XSS attacks, developers can sanitize data input by users in an HTTP request before reflecting it back. Another technique that scammers use to add credibility to their story is website cloning they copy legitimate websites to fool you into entering personally identifiable information (PII) or login credentials. A drive-by download can take advantage of an app, operating system or web browser that contains security flaws due to unsuccessful updates or lack of updates. P2 encrypts his message and the messages signed hash using the symmetric key and sends the entire thing to P. P is able to receive the symmetric key from P2 because only he has the private key to decrypt the encryption.
It involves impersonating a trusted person or entity, and tricking individuals into granting an attacker sensitive information, transferring funds, or providing access to systems or networks. Kaseya, a US-based provider of remote management software, experienced a supply chain attack, which was made public on July 2, 2021. Advanced Bot Protection Prevent business logic attacks from all access points websites, mobile apps and APIs. Others are hacktivists acting in the name of social or political causes. Cybersecurity regulatory compliance entails adhering to several measures to safeguard data confidentiality, integrity, and accessibility. This is because servers consume all available resources to respond to the request overload. Firewalls and network security solutions can help protect against small-scale DoS attacks. The attacker then uses the rootkit to steal passwords, keys, credentials, and retrieve critical data. Unlike many other types of cyber security attacks, a drive-by doesnt rely on a user to do anything to actively enable the attack you dont have to click a download button or open a malicious email attachment to become infected. XSS attacks use third-party web resources to run scripts in the victims web browser or scriptable application. Two weeks after the events, the US Justice Department charged three suspects, one of whom was 17 years old at the time. Social engineering is an attack vector that relies heavily on human interaction, used in over 90% of cyberattacks. Another purpose of a DoS attack can be to take a system offline so that a different kind of attack can be launched. Top 10 Cyber Attack Maps and How They Can Help You. Ransomware is malware that uses encryption to deny access to resources (such as the users files), usually in an attempt to compel the victim to pay a ransom. A variation on phishing is spear phishing, where attackers send carefully crafted messages to individuals with special privileges, such as network administrators, executives, or employees in financial roles. Rootkits are installed inside legitimate software, where they can gain remote control and administration-level access over a system. phishing cyber spear threats infographic attack could outlook virus cyberattack alert windows fool wise even still cyberwarzone trends re australia As many as 43% of small businesses do not have any cyber defenses in place. Attack Analytics Ensures complete visibility with machine learning and domain expertise across the application security stack to reveal patterns in the noise and detect application attacks, enabling you to isolate and prevent attack campaigns. Zero-day attackers jump at the disclosed vulnerability in the small window of time where no solution/preventative measures exist. The attackers computer continues dialog with the server and the server believes it is still communicating with the client.
By accessing a persons password, an attacker can gain entry to confidential or critical data and systems, including the ability to manipulate and control said data/systems. A DDoS attack is also an attack on systems resources, but it is launched from a large number of other host machines that are infected by malicious software controlled by the attacker. Stop external attacks and injections and reduce your vulnerability backlog. They used social engineering attacks to steal employee credentials and gain access to the companys internal management systems, later identified by Twitter as vishing (phone phishing). cybersecurity threats dealing pakistan cyber javed muhammad mubeen Threat intelligence operates in the background and supports many modern security tools.
In the Netwrix blog, Jeff shares lifehacks, tips and tricks that can dramatically improve your system administration experience. A DDoS protection system or service monitors traffic to detect a DDoS attack pattern, and distinguish legitimate from malicious traffic. IP packets of this size are not allowed, so attacker fragments the IP packet. This type of attack usually involves submitting malicious code into an unprotected website comment or search box.
At the same time, organizations of all sizes are facing a global cybersecurity skills shortage, with almost 3.5 million open jobs worldwide, 500,000 of them in the US alone. Birthday attacks are made against hash algorithms that are used to verify the integrity of a message, software or digital signature. Cookie Preferences Trust Center Modern Slavery Statement Privacy Legal, Copyright 2021 Imperva. Measures to mitigate these threats vary, but security basics stay the same: Keep your systems and anti-virus databases up to date, train your employees, configure your firewall to whitelist only the specific ports and hosts you need, keep your passwords strong, use a least-privilege model in your IT environment, make regular backups, and continuously audit your IT systems for suspicious activity. Make sure all data is validated, filtered or escaped before echoing anything back to the user, such as the values of query parameters during searches. Once the target system reassembles the packet, it can experience buffer overflows and other crashes. DoS attacks work by flooding systems, servers, and/or networks with traffic to overload resources and bandwidth. Hear from those who trust us for comprehensive digital security. In a recent survey, 78% of respondents said they believe their companys cybersecurity measures need to be improved. Rootkits are commonly spread through email attachments and downloads from insecure websites. cyber history security attacks usps possible package track Access to a persons password can be obtained by looking around the persons desk, sniffing the connection to the network to acquire unencrypted passwords, using social engineering, gaining access to a password database or outright guessing. The term malware encompasses various types of attacks including spyware, viruses, and worms. Phishers often leverage social engineering and other public information sources to collect info about your work, interests, and activitiesgiving attackers an edge in convincing you theyre not who they say. These vulnerabilities enable attackers to forge untrusted URLs, use them to access an Exchange Server system, and provide a direct server-side storage path for malware. In one IoT attack case, a Vegas casino was attacked and the hacker gained entry via an internet-connected thermometer inside one of the casinos fishtanks. Fill out the form and our experts will be in touch shortly to book your personal demo. hacking With so much confidential and personal information being shared online, its not surprising that data breaches have become more common. A short time after the attack, press reports said 800-1500 small to mid-sized companies were infected by REvil ransomware as a result of the attack. Threat intelligence databases contain structured information, gathered from a variety of sources, about threat actors, attack tactics, techniques, and procedures, and known vulnerabilities in computing systems. xss attacks cybersecurity The attackers used the stolen accounts to post bitcoin scams and earned more than $100,000. There are different types of DoS and DDoS attacks; the most common are TCP SYN flood attack, teardrop attack, smurf attack, ping-of-death attack and botnets. attacks frontiersin strim These DDoS attacks are difficult to trace because botnets are located in differing geographic locations. Ransomware is one of the most prevalent types of attacks, with some attacks using extortion techniques, such as threatening to expose sensitive data if the target fails to pay the ransom. The name phishing alludes to the fact that attackers are fishing for access or sensitive information, baiting the unsuspecting user with an emotional hook and a trusted identity. From there, cyber attackers can steal and manipulate data by interrupting traffic. A WAF protects web applications by analyzing HTTP requests and detecting suspected malicious traffic. b110 bukidnon malaybalay infobae Integrate with any database to gain instant visibility, implement universal policies, and speed time to value. While some bots are useful (such as bots that index websites for search engines), others can perform malicious activities. stealing damaging intent devices The attack can be performed by an individual or a group using one or more tactics, techniques and procedures (TTPs). While XSS can be taken advantage of within VBScript, ActiveX and Flash, the most widely abused is JavaScript primarily because JavaScript is supported widely on the web. However, if the attacked resource belongs to a business competitor, then the benefit to the attacker may be real enough. The attack compromised an update meant for SolarWindss software platform, Orion. The malware exploiting these vulnerabilities was pushed to customers using a fake software update labelled Kaseya VSA Agent Hot Fix. Jeff is a former Director of Global Solutions Engineering at Netwrix. Securing databases involves hardening database servers, properly configuring databases to enable access control and encryption, and monitoring for malicious activities. A replay attack occurs when an attacker intercepts and saves old messages and then tries to send them later, impersonating one of the participants. These bots or zombie systems are used to carry out attacks against the target systems, often overwhelming the target systems bandwidth and processing capabilities. Client-Side Protection Gain visibility and control over third-party JavaScript code to reduce the risk of supply chain fraud, prevent data breaches, and client-side attacks. cyber points security attacks list business All APIs, especially public APIs that are accessed over the Internet, are sensitive to attacks. Generally, encryption and digital certificates provide an effective safeguard against MitM attacks, assuring both the confidentiality and integrity of communications. It is considered one of the largest DDoS attacks in history. The complexity and variety of cyberattacks are ever-increasing, with a different type of attack for every nefarious purpose. Certificate authorities and hash functions were created to solve this problem. The attacker can also modify messages before sending them on to the intended recipient. Top 10 Most Common Types of Cyber Attacks, 1. Black hole filtering, which drops undesirable traffic before it enters a protected network. The attackers computer gains control of the client. It occurs when a malefactor executes a SQL query to the database via the input data from the client to server. It does this by maintaining a large database of known bot sources, and detecting behavior patterns that might indicate a bot is malicious. Then, anyone wanting to send an encrypted message to P using Ps public key is unknowingly using As public key. What Is a Distributed Denial of Service (DDoS) Attack? Another option would be to configure the end systems to keep them from responding to ICMP packets from broadcast addresses.